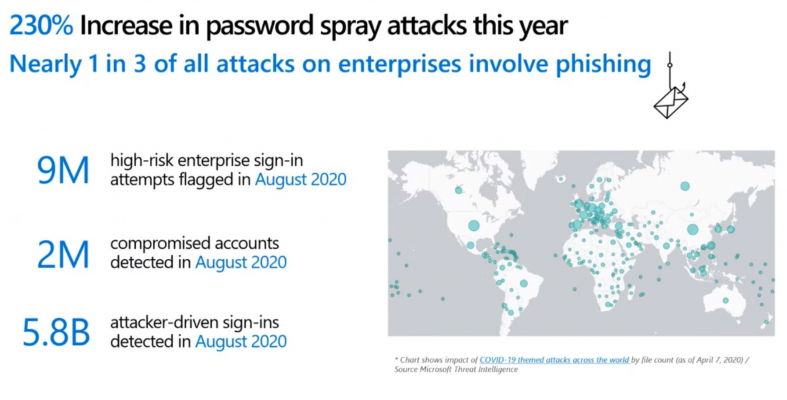
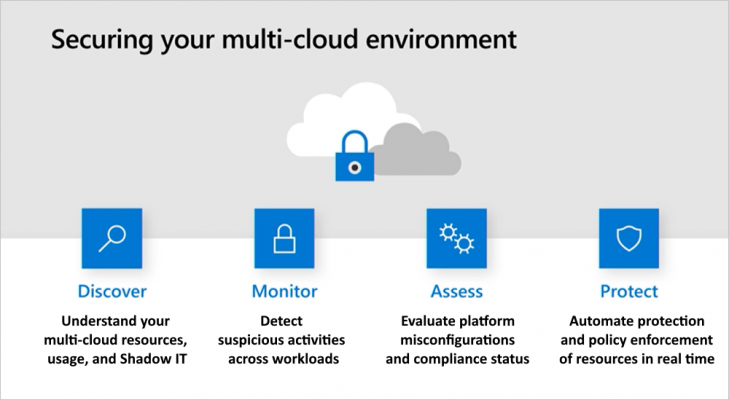
Over Last few years there has been a large rise in identity based attacks and breaches. Company network perimeters have been broken down with the rise of remote working and Bring-your-own-devices (BYOD), the modern workplace brings more security criteria for businesses to consider.
(Image Credit: Microsoft)
Alongside those mentioned above there is a large gap with multivendor Cloud and 3rd party applications where Identity management can add extra risk. Remembering passwords for three of the big cloud providers and any 3rd party apps your business uses can leave users, using either the same password or making passwords similar that are easy to crack and breach. It also leaves you looking at multiple security centres and configurations.
Wouldn’t it be great if you could manage your entire Identity Access Management (IAM) suite in one place?
Even better if one IAM suite had the ability to configure security controls, identify risk, automatically learn, and respond and keep your administrators up to speed with what’s going on across your cloud platforms?
With Microsoft Zero Trust line-up this is all possible. For sure Single-Sign-On (SSO) has been around for a while, but in this blog I’m going to talk about multi-cloud SSO and the potential benefits Azure Active Directory (AAD) and Microsoft Defender for Identity – part of the Microsoft 365 (M365) Defender services suite – could bring to your organisation. We will leave device management, cloud apps security and information protection for future blogs.
(Image Credit: Microsoft)
Even without using a Zero Trust Principled Architecture, there are still security gains that can be made around Identity management. If we take the “Verify Explicitly” principle, where we would verify User Location and Device Health, we can apply some level of monitoring to any AAD user within our tenant. However, you’ve then got a separate account for the other big cloud providers outside of Azure, which you would need to monitor within those platforms’ IAM systems. So why not link AAD to AWS (as an example, other cloud platforms are available) and use AAD as your Identity provider, meaning your users have the simplicity of being able to use their standard Microsoft (AAD) account to login to the AWS Workspace. With this Setup:
- Roles are all defined within AWS meaning you can build specific roles to control User and Admin access to the levels you require.
- These Roles are pulled through to AAD and can be managed by the standard Group Role Assignment within AAD.
- Users then get added to the groups giving them the access they require.
The beauty of using the Microsoft Defender for Identity is you can set up conditional access based around the criteria you select, Session Risk, User Risk and Locations to name (just a few.) You can utilise the Microsoft Security Information and Event Management (SIEM) called Azure Sentinel, that can sit over the top of the M365 Defender suite to re-assess these risk’s continually, meaning the level of security and control you can apply to AWS logins is to a safe standard you would like.
Again, for sure this can be done in most cases with each platforms’ IAM Security Suite but it’s more management for administrators from a security point of view and more cost for the business due to running multiple IAM Security Suites.
If you’re interested in how we could help you around IAM, please reach out to us!